Source code for USB HID and CDC libraries and examples are downloadable from the CC2531 product page on www.ti.com. Combined with the industry-leading and golden-unit-status ZigBee protocol stack (Z-Stack) from Texas Instruments, the CC2531 provides a robust and complete ZigBee USB dongle or firmware upgradable network node. Bus 001 Device 009: ID 0451:16b3 Texas Instruments, Inc. Device Descriptor: bLength 18 bDescriptorType 1 bcdUSB 2.00 bDeviceClass 0 (Defined at Interface level) bDeviceSubClass 0 bDeviceProtocol 0 bMaxPacketSize0 32 idVendor 0x0451 Texas Instruments, Inc. IdProduct 0x16b3 bcdDevice 90.07 iManufacturer 1 Texas Instruments iProduct 2 CC2540 USB. Dvi: InfName - c: texas instruments ble-cc254x-1.4.2.2 accessories drivers ccxxxxusbcdc.inf dvi: DevDesc - TI CC2540 USB CDC Serial Port dvi: DrvDesc - TI CC2540 USB CDC Serial Port dvi: Provider - Texas Instruments dvi: Mfg - Texas Instruments dvi: ModelsSec - DeviceList.NTamd64 dvi: InstallSec - DriverInstall dvi: ActualSec - DriverInstall.
| Project CC2540 | |
|---|---|
| Reverse engineering the CC2540 BLE sniffer dongle | |
| Status | Stalled |
| Contact | bertrik |
| Last Update | 2018-05-13 |
- 3Analysis
- 4Protocol
- 4.2Reading BLE frames
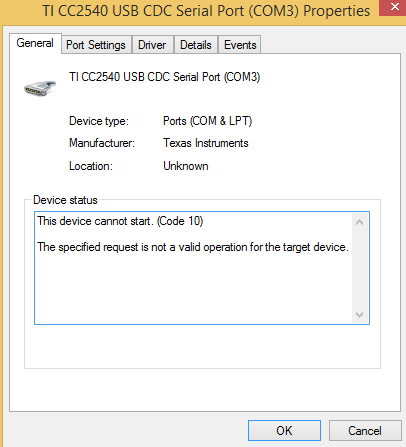
- But I cannot find the 'TICC2540 usb cdc serial port' in my Device manager. I first download CC2640SmartRFHostTestReleaseAll.hex and the download app & stack. If I download app & stack first, 'CC2640SmartRFHostTestReleaseAll.hex' will failed to be download. If there is anything wrong with the usb driver?
- Description The CC2540 USB Dongle is a complete example of how to use the USB enabled Bluetooth Low Energy (BLE) Wireless MCU. The reference design can be used to enable Bluetooth Smart and Internet of Things applications on any system that contains a USB host.
Status
At this point (2017-05-09), the status is:
- it is pretty clear which commands the default sniffer firmware understands
- I wrote a little test program to dump raw BLE frames
- there is no plugin for WireShark yet
Introduction
This page is about the CC2540 bluetooth low-energy sniffer dongle and getting it to work with Linux.A nice end result could be that it becomes possible to sniff directly in WireShark with this dongle.
I have such a 'WeBee' dongle that can be found for about E15,- on websites like Aliexpress.
It's supposedly a CC2540 (or compatible) dongle, the USB id is 0451:16b3.
Interesting links:
Analysis
USB descriptor
When plugging this stick into a Linux machine, you can see it uses only one bulk endpoint.

Reading the identification from the stick with the 0xC0 command, results in the following 8-byte response
You can recognise the 2540 type number in there.
USB logs from Windows
This USB device does actually work with Windows:
I've captured a log of the communication over USB while the BLE is capturing bluetooth traffic from some iBeacon, using USB pcap.
In the logs, I cannot see any firmware blobs being downloaded to the stick.Probably the stick comes with a pre-loaded firmware of itself to do the BLE sniffing.
The USB control transfer request codes seem to match up with the code in https://github.com/christianpanton/ccsniffer/blob/master/ccsniffer.py
- 0xC0, GET_IDENT: returns some kind of identifier
- 0xC5, SET_POWER
- 0xC6, GET_POWER
- 0xC9, no idea, this appears in my USB logs but I can't find it in the python code
- 0xD0, START
- 0xD1, STOP
- 0xD2, SET CHAN
Protocol

In the windows sniffer software, it seems there are only two things communicated:
- towards the stick: which radio channel to sniff, and some other radio settings
- from the stick: raw sniffed BLE frames
Configuring the radio
This appears to be done using USB control transfers.
The following requests are sent:
| Request type | Request | Value | Index | Data | Description |
|---|---|---|---|---|---|
| 0x40 | 0xC5 | 0 | 4 | - | Set power |
| 0xC0 | 0xC6 | 0 | 0 | 0x00 | Get power |
| 0xC0 | 0xC6 | 0 | 0 | 0x04 | Get power |
| 0x40 | 0xC9 | 0 | 0 | - | ??? |
| 0x40 | 0xD2 | 0 | 0 | 0x27 | Set channel |
| 0x40 | 0xD2 | 0 | 1 | 0x00 | Set channel |
| 0x40 | 0xD0 | 0 | 0 | - | Start capture |
Request type 0x40 is a vendor-specific device request from host-to-device.Request type 0xC0 is a vendor-specific device request from device-to-host.
Reading BLE frames
This appears to be done using USB bulk input transfers.
Driver Ti Cc2540 Usb Cdc
I can see a lot of similarities between the USB log and the BLE sniffer log.
Each frame starts with a byte indicating the type of frame, following by two bytes indicating the length of the rest of the frame (encoded as little endian).
data frames
The bulk USB data starts off with two bytes indicating the length of the rest of the data.
In the example image on the right:
- 00: 0 means this is a data frame
- 31 00: length of rest of frame encoded in little endian = 49 bytes decimal
- 39 04 29 54: part of the time stamp
- 2c d6 be ..: data frame contents
unknown frames (tick or 'alive'?)
The stick also returns 4-byte frames, alternating between
and
Interpretation:
- 01: 1 means this is a frame of type 1
- 01 00: length of the rest of the frame encoded in little endian = 1 byte
- 40 or C0: unknown data byte
Software
Preliminary code can be found athttps://github.com/bertrik/cc2540
It connects to the dongle and dumps raw USB packets to stdout.
Cc2540 Driver
This software requires libusb-1.0-dev